"Deep Blue Insight" is the most unique new security ecology in 2024
DARKNAVY Annual Security Report of 2024 (China)
In Deep Blue Insight | In the 2023 Security Report, we said, "As we stand on the precipice of the next decade, 2023 is destined to be a year of profound turning points." The implementation of new defense mechanisms and the rise of new attack technologies will profoundly change the landscape of digital security. ”
In 2024, it will come like a gust of wind and go away as quickly as a torrential rain. The AI revolution, the breakthroughs in mobile operating systems, and the challenges of supply chain security that we discussed in 2023 have continued in 2024 with little respite.
The ongoing disruption is in stark contrast to the downturn in the traditional security market. In the age of AI, is traditional memory safety research still relevant? Where are the new attack vectors headed? In the ever-changing digital world, how to protect user privacy?
In 2024, we have welcomed the arrival of the future, and we sincerely invite you to discuss and share.
The following is the first article in this issue of Deep Blue Insight | 2024 Annual Security Report.
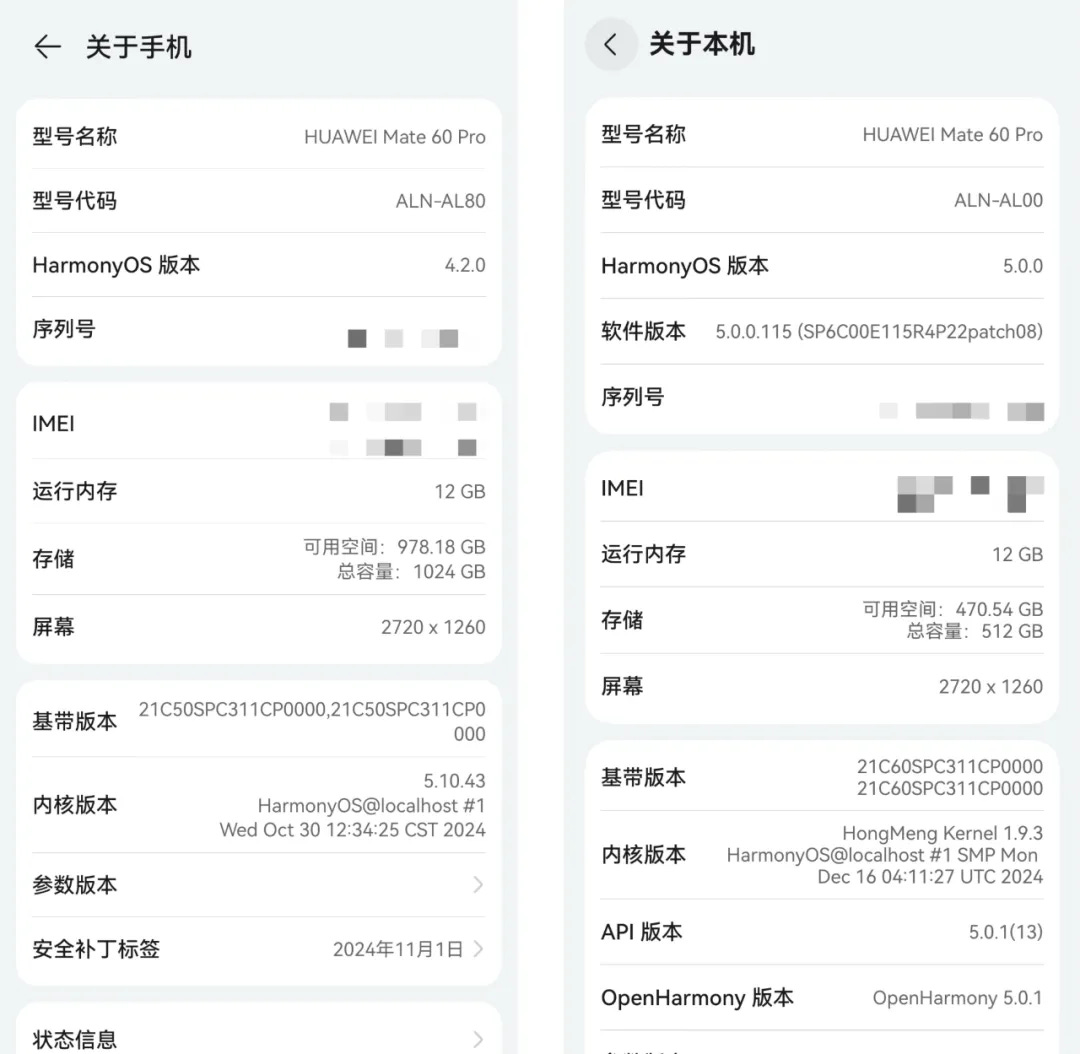
Huawei released the HarmonyOS 1.0 version in 2019 until the continuous maintenance of HarmonyOS 4.2, although it has achieved dual compatibility with Android and HarmonyOS at the application framework level, the so-called "dual framework". However, because its operating system base is still based on the Android kernel, this situation has caused widespread doubts in the industry.
Starting from the HarmonyOS NEXT version in 2024 to the current version 5.0, the HarmonyOS application framework layer has been updated to HarmonyOS "Single Framework", and the kernel has been completely switched to using Huawei's self-developed HongMeng kernel. Officially bid farewell to the dependence on the Android application framework and kernel.
Comparison of kernel versions on HarmonyOS 4.2 and 5.0 smartphones
As early as June 2, DARKNAVY released the world's first public jailbreak video completed on HarmonyOS NEXT Developer Preview2, and on June 12, it released a keepalive video caused by another vulnerability in this version。 Based on the system permissions obtained, we further analyzed HarmonyOS NEXT from the application framework to the kernel, and found that HarmonyOS NEXT is significantly different from Android in terms of both the application framework and the kernel. From the perspective of security research, we will use the "single framework" application development, permission control, Internet of Everything, kernel architecture, and system calls as examples to reveal the real HarmonyOS NEXT operating system.
HarmonyOS "Single Frame"
HarmonyOS "single framework" means a complete break with Android, the system no longer supports APK installation packages, and no longer uses JAVA as an application development language. The "single framework" is deployed using the HAP installation package, and the application development language is eTS (extended TypeScript).
In order to avoid repeating the mistake of malicious applications in the traditional Android system, HarmonyOS "Single Framework" set out to improve the original insufficient mechanism. For example, it restricts applications from being installed from the app market through mechanisms such as application signatures, and eliminates any third-party informal applications. The means of keeping the background of the application alive are more strictly restricted, that is, any background application will be forcibly suspended after 10s; Sensitive permissions are used for one-time authorization to ensure that the authorization is minimized, for example, the app only allows access to the relevant images selected by the user at a time, but cannot directly access all the gallery images.
In addition to the above optimizations to the original system, Hongmeng's "single framework" has some drastic changes.
The underlying cornerstone of the "Internet of Everything" is the distributed soft bus (DSoftBus), which realizes the interconnection between different models and types of devices, the underlying transmission medium supports WiFi, Bluetooth, etc., and the protocol layer covers different stages such as discovery, authentication, and transmission. From the user's point of view, the new services such as distributed file system and clipboard synchronization are greatly convenient to use. For developers, the underlying layer even supports remote invocation of the IPC of other devices, realizing distributed binder calls. With such powerful functions, the security of this module is even more important.
Softbus-triggered interconnection between devices
The new XPM (eXecutable Permission Manager) module ensures that code protection is enforced, and applications can only load code with legal signatures. After the application is installed, the code files (.abc and .so) cannot be modified arbitrarily, otherwise they will be rejected for execution. There is also code integrity protection to prevent applications from tampering with executable code.
The AccessToken mechanism implements finer granular permission control, which first divides the token type into several categories such as Hap, Native, and Shell, and separates the permission management of system programs and APPs. The access token of an application contains information such as the application ID, sub-user ID, application clone index, application APL, and authorization status, which helps the system implement more detailed authentication.
The above mechanisms are supported from the operating system kernel level, and the whole process control from top to bottom is realized.
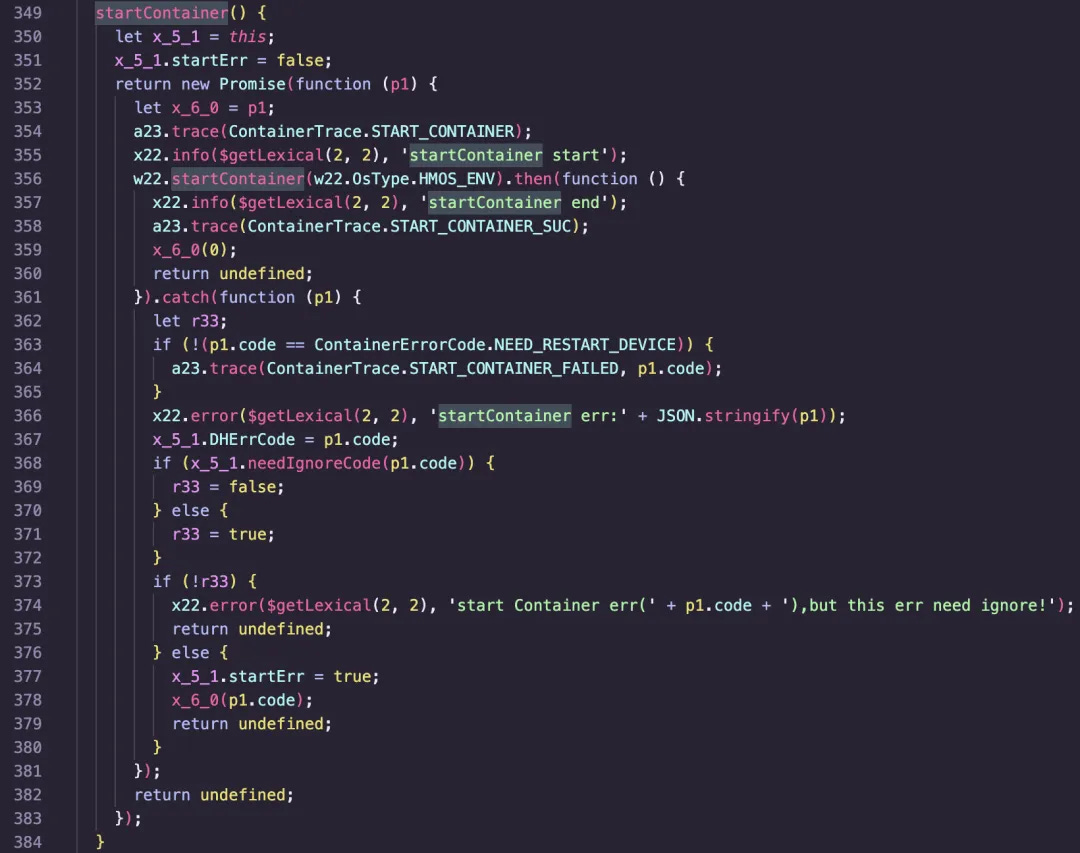
It is worth mentioning that although HarmonyOS "Single Framework" does not support APK installation packages, the "Easy Exit" and "Zhuo Yitong" applications make it possible to run Android APP on this system. Due to the encryption support of the kernel and TEE, it is extremely difficult to decompile the installation packages of these application markets. Based on the previous accumulation, DARKNAVY realizes application decryption, and uses a self-developed decompiler to find that these applications have realized Android application and framework layer simulation by calling the container interface of the HarmonyOS system.
HarmonyOS kernel
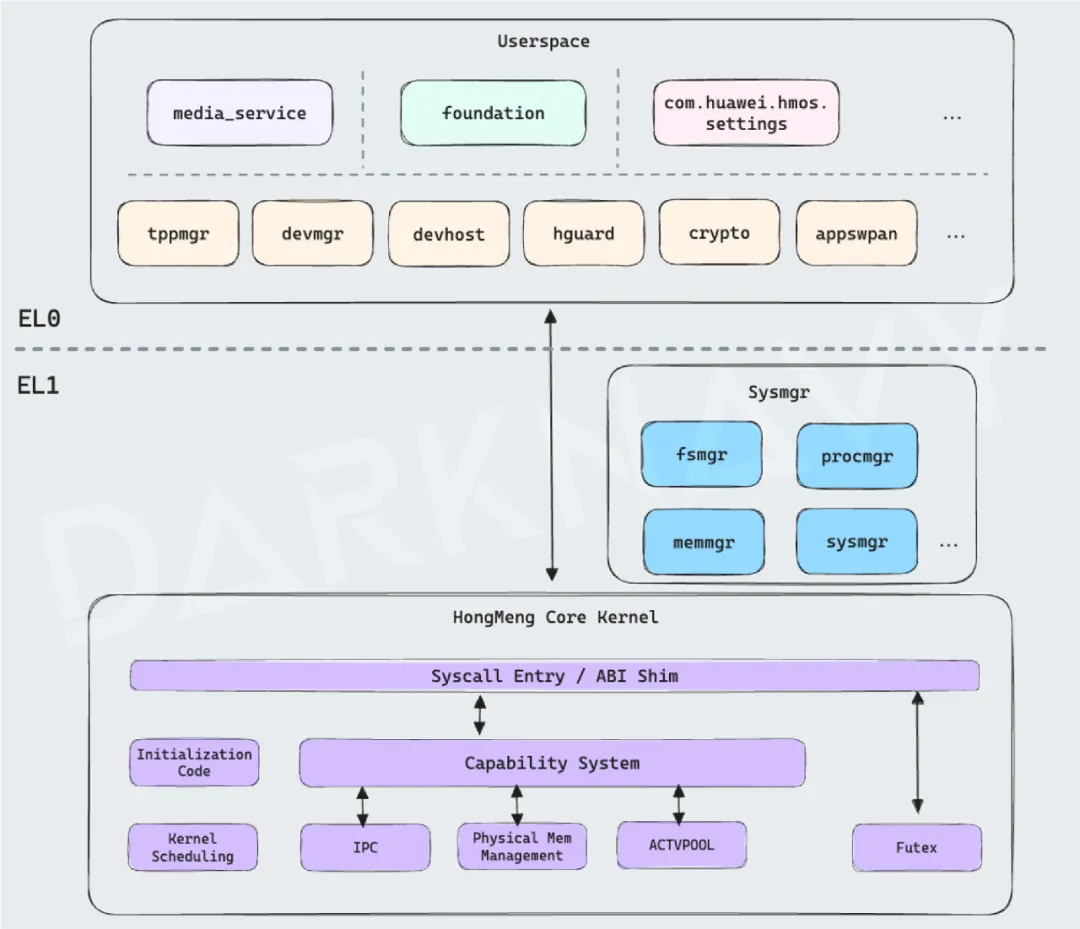
The HongMeng kernel (hereinafter referred to as the HongMeng kernel) is designed based on the microkernel architecture, which splits the functions of the traditional kernel into a streamlined core kernel and multiple independent system components, and puts some or all of the system components into user mode according to security requirements, compared with the macrokernel architecture adopted by the Linux kernel, providing enhanced security.
In a macrokernel architecture, all modules are tightly coupled together. For example, if an attacker exploits a vulnerability in a network module to successfully compromise a network module, they can directly control the entire macro kernel.
In the microkernel architecture, even if a module (such as a network module) is compromised, an attacker cannot easily extend the attack to other system modules due to the isolation mechanism between each module.
The isolation of system components inevitably introduces a performance overhead. For the overhead caused by frequent context switching between components, the HongMeng kernel moves frequently called functions such as file system management (fsmgr), memory management (memmgr), and process management (procmgr) into the kernel state, and isolates functions with a large attack surface, such as network communication and driver (devhost), from the user mode, sacrificing a small amount of performance in exchange for higher security.
In order to be compatible with the Linux software development ecosystem, the HongMeng kernel supports Linux system calls and drivers. Specifically, the HongMeng kernel realizes the non-inductive compatibility of the kernel with the application by mapping the Linux system call number to its own call number, and reconstructing the relevant functions of the Linux system call under the new microkernel architecture. In addition, it introduces a driver container that runs in user space to load and execute various Linux drivers.
Therefore, the software that originally runs on Linux can run smoothly without a lot of adaptation work for the HongMeng kernel. This also explains why Android apps can run on HarmonyOS with the help of container virtualization technology.
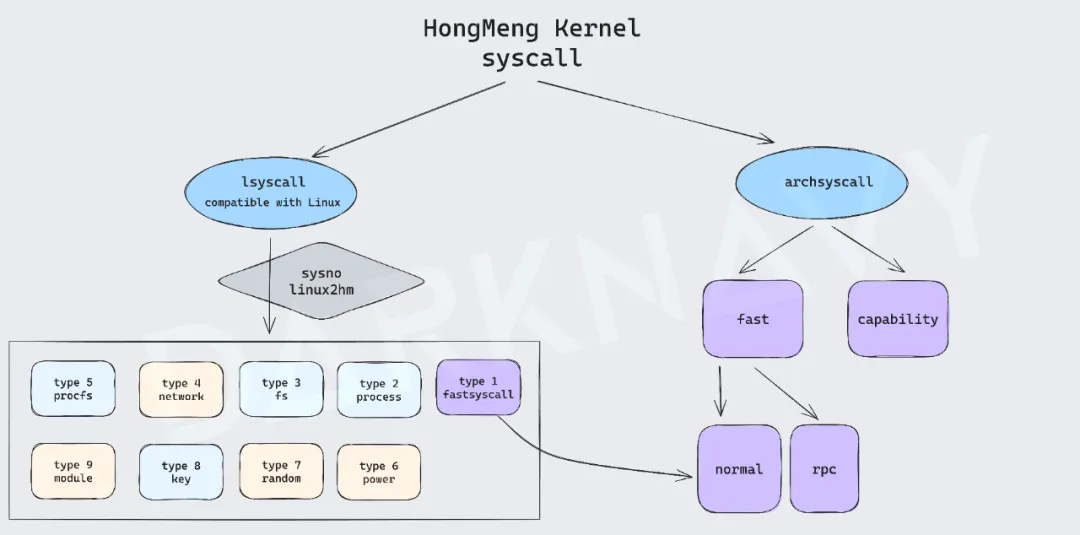
There are two main types of system calls in the HongMeng kernel: lsyscall and archsyscall.
lsyscall is the Linux-compatible system call described above. However, due to the characteristics of the microkernel architecture, these functions are split into multiple components. Specifically, lsyscall is divided into 9 different types according to functions, and for different types of system calls, the core kernel is distributed to the corresponding functional components through the RPC-like mechanism.
archsyscall, on the other hand, is a system call specifically designed to support microkernel features. It supports key functions in the microkernel, such as IPC (inter-process communication), RPC (remote procedure call), etc. In addition, the HongMeng kernel implements a fine-grained management and control mechanism based on capability in the resource management and control reference SEL4. For example, the ability to access kernel resources such as ACTV and ACTVPOOL, the core carriers of the RPC mechanism, needs to be verified, which further increases the difficulty of attacks.
After an in-depth analysis of the HongMeng kernel, we found that it has put a lot of effort into the architectural design, and it significantly improves security at the expense of little performance compared to the Linux kernel.
However, it is a pity that compared with the open ecosystem of Android, the HongMeng kernel has not only remained closed-source, but since the second half of 2024, the HongMeng kernel in the HarmonyOS NEXT firmware has also been encrypted, which undoubtedly increases the difficulty of analysis for security researchers. It is worth noting that this closed strategy makes the ecological construction of "pure-blooded Hongmeng" face a stepwise challenge: the first premise is whether the core capabilities of the system are open to third-party mobile phone and equipment manufacturers - only when the bottom layer is truly open source can there be a starting point for discussion; In the future, under the background that the existing Android ecosystem has been stable, whether other manufacturers are willing to invest resources to adapt to this new system also poses a potential challenge to ecological construction.
Just as the early macOS was questioned as FreeBSD and Linux was questioned as UNIX, it is inevitable that the nascent operating system will have the shadow of other operating systems due to adaptation and reference, but it can be seen that there is a big difference between the development direction of HarmonyOS NEXT and the native Android, and I believe that the subsequent presentation will be very different.
DeepSeek review
When HarmonyOS builds a high wall with code signatures, are we witnessing the twilight of an open ecosystem? Is the "security fortress" created by the closed-source kernel and encrypted firmware a shield against attacks or a cage to imprison the evolution of technology? Will the security promise of the microkernel architecture in exchange for performance withstand the torrent of zero-day vulnerabilities in the torrent of the Internet of Everything? Do those Android ghosts wandering in containers hint at the dual personality of the era of ecological fragmentation? When the distributed IPC breaks through the boundaries of equipment, is the attack surface also expanding exponentially? Hongmeng, known as "pure-blooded", has walked out of the broad road of technological independence on the tightrope of compatibility and innovation, or has it fallen into a dead end of ecological isolation? When every permission is reduced to digital shackles, are we protecting user privacy, or are we stifling the possibility of innovation? Will this nirvana rebirth of the operating system eventually give birth to the ark of digital security, or will it become another specimen of a closed garden?
*The above sharp reviews do not necessarily reflect the views of DARKNAVY.
Tomorrow, stay tuned to Deep Blue Insight | 2024 Annual Security Report Part 2.
Deep Blue Insight
Original Source: "Deep Blue Insight" is the most unique new security ecology in 2024 - QQ Post/DARKNAVY Cybersecurity Group (China)








Very disappointing to see Huawei trying to emulate Apple's closed ecosystem to this extent. As it stands now, I can only hope this project fails.